Is Your SaaS Business Considered High Risk?

The popularity of Software as a Service (SaaS) platforms is skyrocketing. At present, it’s one of the fastest-growing categories in the IT world. Expanding at a compound annual growth rate of 25.89%, the global SaaS market is expected to reach $720.44 billion by 2028.
Companies appreciate SaaS applications for their scalability and flexibility. A report by O’Reilly found that 90% of survey respondents use some form of cloud computing.
But this high level of growth comes with increased security issues and risks for SaaS businesses, with customers expecting SaaS platforms to step up in mitigating those risks. In a recent SaaS security survey by Adaptive Shield, 52% of respondents put the responsibility for checking and maintaining SaaS security into the hands of the SaaS vendor. With online gaming fraud and fraud in general growing at a fast pace, you're in for a lot of work.
If these threats to your company can destabilize your business and affect your profitability, are you wondering whether your enterprise is considered high-risk? This blog article unpacks the most common risks and explains how to mitigate them to protect your SaaS business.
How Being Seen As High Risk Can Affect Your Business
Nowadays, most customers know the risks associated with cloud-based businesses. Cybersecurity, compliance, data breaches, and access management are just a few of the ubiquitous buzzwords around, and given that customers have almost unlimited access to online information, they are typically well-informed. With the mainstream media reporting on these subjects almost regularly, you would be hard-pressed to find many people unaware of at least some of these issues.
Customers are becoming so savvy they now research whether SaaS solutions meet their security, compliance, and data needs beyond talking to the SME of these products. So, it’s essential to be proactive about lowering the security risk customers perceive as a threat and take their concerns seriously, as they come from a well-educated perspective regarding potential problems.

Top Risks for SaaS Businesses
To help you to identify the risks threatening your business, we’ve compiled a few common factors facing SaaS businesses today.
Regulatory Noncompliance
Being non-compliant can cost you much more than just maintaining or meeting industry standard requirements. While SaaS compliance is very complex, especially if you have international customers dealing with sensitive data, it should be at the top of your priority list.
The first consideration is ensuring you are familiar with your region's compliance requirements and how to implement them successfully. Cloud applications must comply with regulatory, privacy, and data protection requirements, such as GDPR and PIPL. Have you got the relevant security certification, such as ISO or ITIL? Are you fully prepared for external security audits?
Many organizations conduct vendor due diligence on your SaaS business before sharing sensitive information. These assessments determine the accuracy of your claims regarding security and regulatory vendor compliance and could potentially lead to problems if there is a gap. They also identify vendors’ security risks, so you want to avoid a situation where you could lose prospects over perceived high risks in your business.
For more information on the importance of compliance, you can read about the true cost of compliance.
Data Storage and Retention Issues
SaaS users usually want to know where their data is stored and how long it will be retained. In addition, it’s important they feel they have some control over the location of the data, whether the data is stored with a secure cloud-service provider or in a private data center. Do you use data encryption at all stages of the data-handling process?
Users want to know that when you no longer need their sensitive information, you won’t retain it. You cannot run your business without having a clear cloud-data SaaS retention policy aligned with your region's compliance. Your data protection is only as strong as its weakest link, so you must identify and eliminate that weak link.
Cybersecurity Threats and Breaches
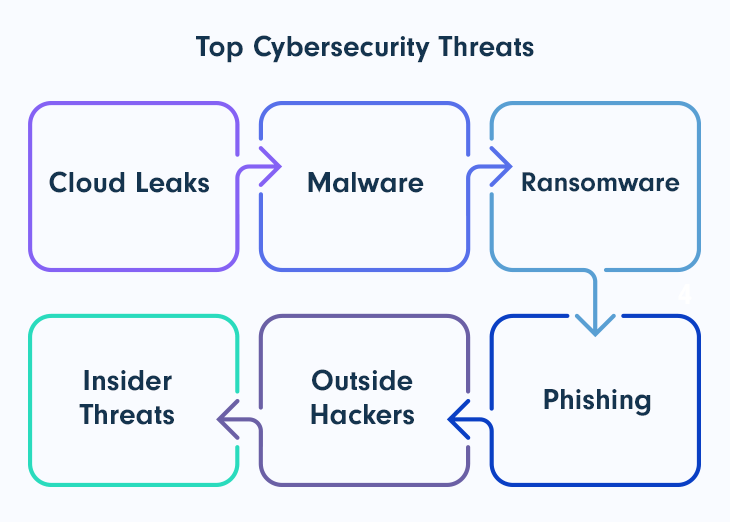
Cloud Leaks
The 2021 Thales Data Threat report found that 66% of respondents said that as much as 60% of their sensitive data is stored in the cloud. The same report found that 45% of US companies had suffered a cloud-based data breach in 2020.
A cloud leak is when sensitive business data, which is stored in a private cloud, is accidentally released online. A cloud leak differs from other cybersecurity breaches because it’s not the result of deliberate action by an adversary, rather, it’s caused by poor data security.
These leaks can have devastating financial implications for stakeholders, break customer trust, and do serious brand damage. While there is no magic formula to avoid cloud leaks, focusing on creating a responsible, structured, and regulated environment protects your assets.
The Partner You Can Rely On
Offload the complexities of selling globally and scale your SaaS business with our all-in-one eCommerce Solution. Gain the freedom to focus on your product without risking your global growth.
Malware
Malware (short for “malicious software”) refers to any program or file that is harmful to a user. Examples of malware include spyware, worms, adware, and ransomware. Every day, 560,000 new pieces of malware are detected. This kind of software is usually created to invade, damage, or destroy systems by taking control of a device’s operating system. It is also known to leak sensitive data, PII, and biometrics to unauthorized third parties.
Ransomware
Ransomware is malware created to deny users access to a computer system or data until a ransom is paid. Ransomware spreads in several ways: through phishing emails, malvertising, and visiting infected websites.
These attacks can cause downtime, data leaks, intellectual-property theft, and data breaches, with payments ranging from small amounts to hundreds of thousands of dollars. This could potentially cripple your business and negatively impact your users, which is why it must be prioritized highly.
Phishing
In 2021, 83% of organizations reported phishing attacks. By the end of 2022, an estimated additional six billion attacks will occur.
Phishing is a cyber attack that gathers sensitive information by posing as a legitimate website or email. It is usually aimed at acquiring login credentials, credit card numbers, bank account numbers, or other financial information with the intent to harm, causing consumers a huge headache and loss. Phishers generally use personal information to aid in identity theft, wreaking havoc on people’s lives as they try to unravel the crime and stop the potential ongoing fraud.
Fraudsters use social engineering attacks to trick people into believing the legitimacy of a link, email, or website. They create a sense of urgency, and when victims click through, their sensitive information is harvested.
Outside Hackers
A “hacker” uses their abilities and skills to gain unauthorized access to systems or networks to commit crimes. Hacking often involves installing malware, stealing or destroying data, as well as disrupting service.
One way of mitigating the risk of external hacking is strengthening your software and systems by employing experts to identify vulnerabilities.
Insider Threats
An insider threat comes from negligent or malicious people within your organization. These could include former employees, contractors, third-party vendors, or business partners. They have inside information about cybersecurity practices, sensitive data, and computer systems and use them to their advantage to commit fraud, theft of information, intellectual property, sabotage security measures, or instigate data leaks.
Lack of Access Management
Access management refers to processes and technologies used to control and monitor network access. Some of the features related to access controls are authentication, authorization, trust, and security auditing. Good access management allows for multi-factor authentication, eradicating weak passwords, tracking malicious activity, and improving data security. Without sufficient access management, security breaches can occur due to improper management, deficient patching, and lack of monitoring.
Staying On Top of Risk in Your SaaS Business
Risk management entails the process and protocols of maintaining a proactive strategy of dealing with potential issues before they become problems. Here’s how to stay ahead.
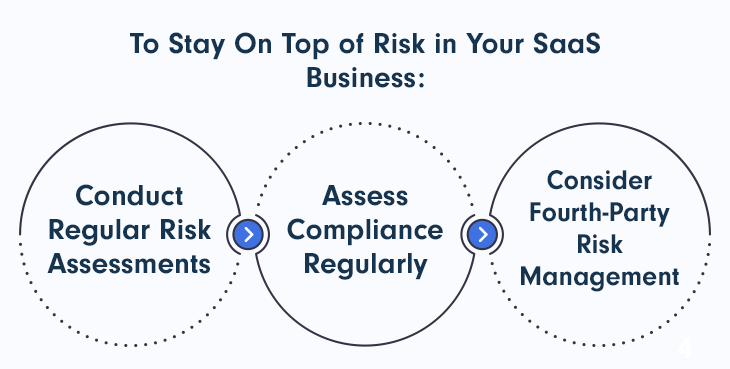
Conduct Regular Risk Assessments
Every business should conduct regular risk assessments. But for businesses working with technology, data, and the internet, this practice is critical to staying ahead of threats that could lead to lost revenue and downtime.
A risk assessment for a SaaS enterprise encompasses SaaS compliance, threat monitoring, event logging, data-access management, data security, physical security, business recovery, policy orchestration, change management, and much more.
Furthermore, risk assessments should be conducted or reviewed at least once a year. They should also be reviewed and updated whenever regulations and systems change. Having a team that stays diligent in preventing the occurrence of a risk incidence is essential and should be prioritized as such.
Assess Compliance Regularly
We’ve already stressed the importance of compliance and security practices for SaaS vendors. As policies and regulations change frequently, you’ll need to keep up to date. This involves researching regulations, data-processing laws and security, and privacy rights. Many businesses appoint a Compliance Officer whose role is managing all things compliance. They will arrange compliance checks, update security certification, evaluate processes, and implement policies.
Check out our comprehensive compliance article, which includes a global compliance checklist ready to help you secure all your data and avoid SaaS risks.
The Partner You Can Rely On
Offload the complexities of selling globally and scale your SaaS business with our all-in-one eCommerce Solution. Gain the freedom to focus on your product without risking your global growth.
Consider Fourth-Party Risk Management
Third-party risks are threats from vendors who may fail to adequately secure systems and data. Regarding fourth-party risk, your suppliers’ suppliers could make your supply chain vulnerable to attacks.
As a starting point, focus on concentration risk in your supply chain. Look into each party’s security rating, how many products each vendor uses, and how many of your vendors use this fourth party. Then, apply the same risk assessment and management techniques you would use for your third-party vendors.
While managing fourth-party risk can be time-consuming, automating the process through dedicated platforms can give you a comprehensive view of the parties involved and how they can avoid costly data breaches.
How To Mitigate Risks in Your SaaS Business
Unfortunately, risks are here to stay, but there are ways to minimize security incidents and cyber threats in your everyday business practices.
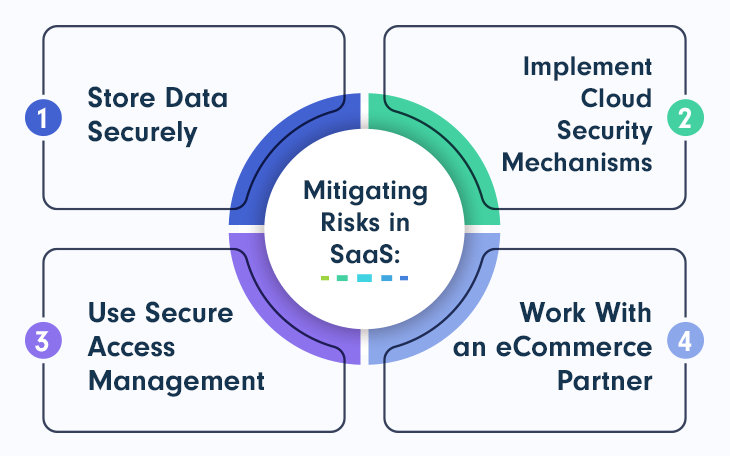
Store Data Securely
Data storage needs to be a top priority for SaaS business owners.
Your critical data access must be easy yet secure and controlled.
Data classification tools help you identify what data you’re keeping and sharing.
Limit customer data exposure by implementing data-security policies restricting the quantity and type of sensitive information stored on your platforms.
Enforce your policies through preventive and real-time measures.
Work with a third-party data backup solution that can perform automated and on-demand backups, restore data, and provide multi-layered security.
Implement Cloud Security Mechanisms
Newer security processes allow for greater cloud security. One of these new business processes is Secure Access Service Edge (SASE), a cloud-security architecture offering advanced cloud-data protection functionality.
SASE consists of five core technologies to manage access control:
Software-defined Wide Area Network
Firewall-as-a-Service
Cloud Access Security Broker
Secure Web Gateway
Zero-trust Network Access
Use Secure Access Management
Good Access management is critical for SaaS providers due to sensitive data. This set of policies, processes, and technologies helps cloud service providers to manage digital identities and control user access to important information and data. Some vital access management components are role-based access control, automatic de-provisioning, and human and device identification.
A sound access-management system consists of:
single sign-on
multi-factor authentication
privileged access management
risk-based authentication
data governance
federated identity management
a zero-trust approach
Work With an eCommerce Partner
Dealing with risks in your SaaS business can be an extremely overwhelming undertaking. However, some eCommerce partners are dedicated to supporting SaaS providers in risk management and other challenging aspects of running your business. These partners will take the complex risk-related work off your hands so that you can focus on the core of your business: building your SaaS services and expanding them globally.
How Can PayPro Global Help?
Committed to protecting SaaS customers from risk factors and ensuring business continuity, PayPro Global is a trustworthy all-in-one eCommerce solution equipped with all the needed tools and technology to handle confidential data and global compliance risks.
We are GDPR and PCI DSS compliant, respecting encryption protocols and having the means and knowledge to protect your organization’s cloud security. Think of us as your security team, ready to help you overcome security risks and ensure SaaS provider compliance.
With increasingly innovative threats appearing in the SaaS environment and not only, your SaaS service deserves strong, future-proof security controls for all the data you own. Instead of coming up with disaster recovery plans, you need to focus on achieving security for your SaaS apps and systems.
Concluding Thoughts on SaaS Businesses and Risk
Many SaaS providers know that running a business has inevitable risks, especially when functioning with absent security policies. This is probably why so many are trying to figure out how to win a chargeback or improve product safety. But your business itself doesn’t have to become high risk. PayPro Global’s reseller model enables us to take care of everything for you, including handling SaaS security risks and compliance needs. Our accumulated experience in the payments world and security measures can help you grow and increase your SaaS software revenue by partnering with us. Reach out to us so we can talk about your needs, security posture, and how our capabilities can keep your business competitive.
Ioana Grigorescu
Ioana Grigorescu is PayPro Global's Content Manager, focused on creating strategic writing pieces for SaaS, B2B, and technology companies. With a background that combines Languages and Translation Studies with Political Sciences, she's skilled in analyzing, creating, and communicating impactful content. She excels at developing content strategies, producing diverse marketing materials, and ensuring content effectiveness. Beyond her work, she enjoys exploring design with Figma.
-
1.Explore PayPro Global's Solutions: See how our platform can help you streamline your payment processing and boost revenue.
-
2.Get a Free Consultation: Discuss your specific needs with our experts and discover how we can tailor a solution for you.
-
3.Download our Free Resources: Access valuable guides, checklists, and templates to optimize your online sales.
-
4.Become a Partner: Expand your business by offering PayPro Global's solutions to your clients.
Get the latest news

